Seems like the bad guys pushing fake antivirus software are not done yet.
We received several reports from the North American region earlier today about users being victimized by a rogue antispyware software. Users download this rogue program after they have somehow been convinced to click on malicious links. These links point to malware that caused overt signs (such as popup balloons and modified wallpapers) to appear on the PC, suggesting that the system has indeed been infected. This is not goodwill, though — downloading the “trial version” only scans the system. To remove the infection, the user will have to purchase the entire antispyware with real money. Users may be infected via spammed email messages, spammed instant messages, or even via ads served in social networking sites.
Soon enough, we’ve discovered not one but two fake antivirus software. This time the attack is made possible through a mass SEO (search engine optimization) poisoning involving several compromised Web sites. This development has certainly upped the chances of the rogue antispyware gaining mileage.
How does this work?
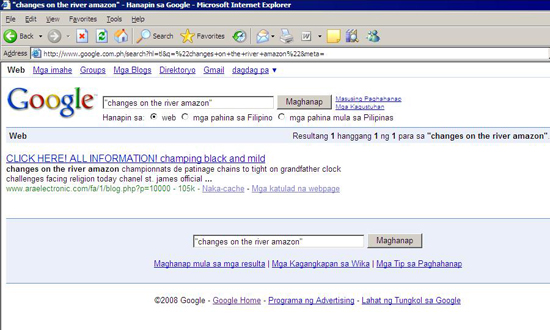
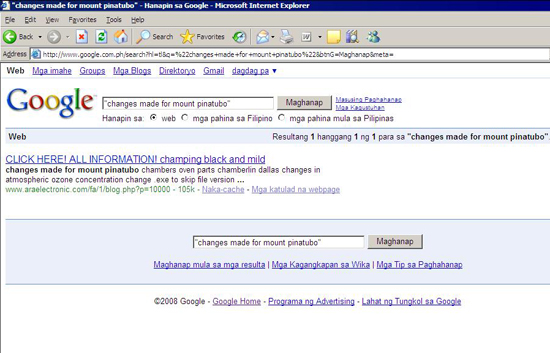
A simple Google/Yahoo! search can lead users to malware-serving site. Search strings such as “changes on the river amazon” or “changes made for mount Pinatubo” will lead them to a malicious Web site. Users who happen to use these strings will find themselves going down the long road of nasty redirections.
Figure 1. Poisoned string leads users to a malware-serving site.
Figure 2. Poisoned string leads users to a malware-serving site.
The two Web sites hosting the malicious pages are normal by themselves, but the exact URL that it points to will automatically redirect to hxxp:// windows-scanner2009. com.
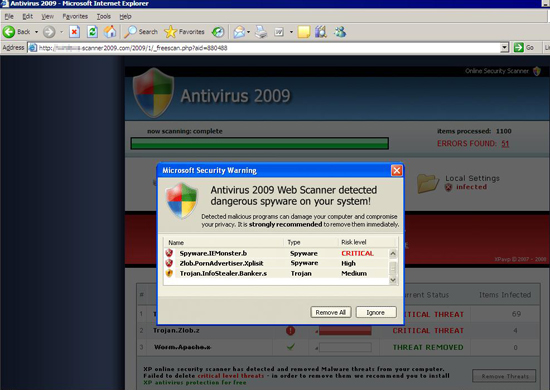
Figure 3. The PC is redirected several times, during which the user begins to see signs that the PC is infected.
Figure 4. Message boxes suggest that the user might want to get rid of viruses in his/her PC by installing a certain software named Antivirus 2009.
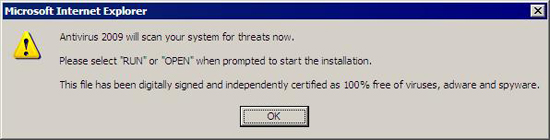
Figure 5. Clicking OK in Figure 4 means the user has agreed to a “free scan.” The message even ends with what should be a comforting note saying that the file is certified free of malware. But don’t be fooled.
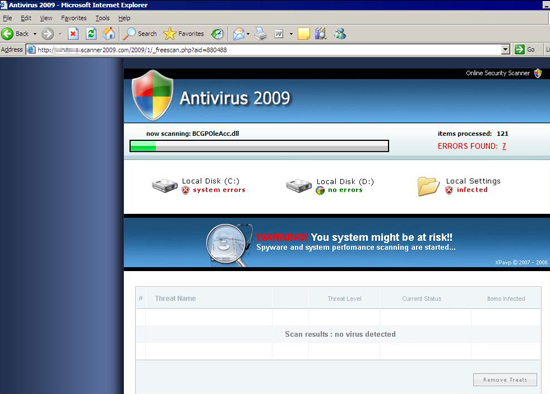
Figure 6. A convincing GUI for Antivirus 2009 performing the system scan might still convince users that they are using legitimate software.
After all the fake notifications, the user will be asked to download the file AV2009Install_880488.exe, which is detected by Trend Micro as TROJ_FAKEAV.DM.
The other fake antivirus will lead users to hxxp://scan. free-antispyware-scanner. com instead of the earlier example.
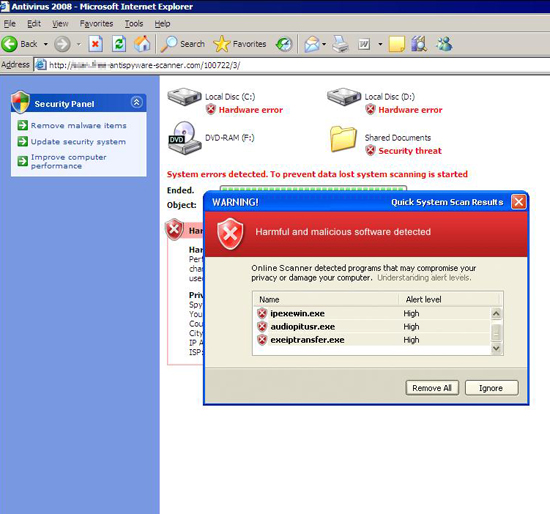
Figure 7. Variation on the rogue antispyware scam.
This will ask the user to download setup_100722_3.exe (detected as TROJ_FRAUDLOA.WM) instead of AV2009Install_880488.exe. (Note that the final agenda for both and most rogue antispyware scams is extortion. Users who fall for this scam pay a certain amount of money to the malware writers to purchase the full version of the fake antispyware.)
According to our investigation, there are about several dozen domains involved that are currently compromised. The hackers were able to upload PHP scripts that contain various text strings designed for SEO poisoning (manipulating or influencing the natural page rankings of search results in order to get more hits than a page really deserves).
This is not the first time Trend Micro has seen this incident — a previous SEO poisoning of this scale was also discovered back in December 2007, with SEO poisoning pages hosted on Blogspot. This time around, compromised Web sites were used instead.
Digging a little bit deeper, we’ve also found that the hackers have almost 1 million search phrases at their disposal for SEO poisoning. These search phrases cover the range from “free downloads, lyrics, travel, politics” and anything in between.
Malicious sites have “CLICK HERE! ALL INFORMATION!” and “CLICK HERE! WANT TO KNOW MORE ABOUT” as their page titles, so it is best to avoid clicking through Google/Yahoo! results that have those aforementioned site titles.














No comments:
Post a Comment